SVE-2019-13963 : Remote stack overflow in Samsung baseband caused by malformed IMMEDIATE ASSIGNMENT message
Posted on Mon 07 December 2020 in Advisory • Tagged with vulnerability, advisory, samsung, shannon, baseband, security, arm
Description
When Samsung Shannon baseband receives message IMMEDIATE ASSIGNMENT (9.1.18 in GSM/04.08) from network, the length of the Mobile Allocation IE (GSM/04.08 10.5.2.21) is not properly checked.
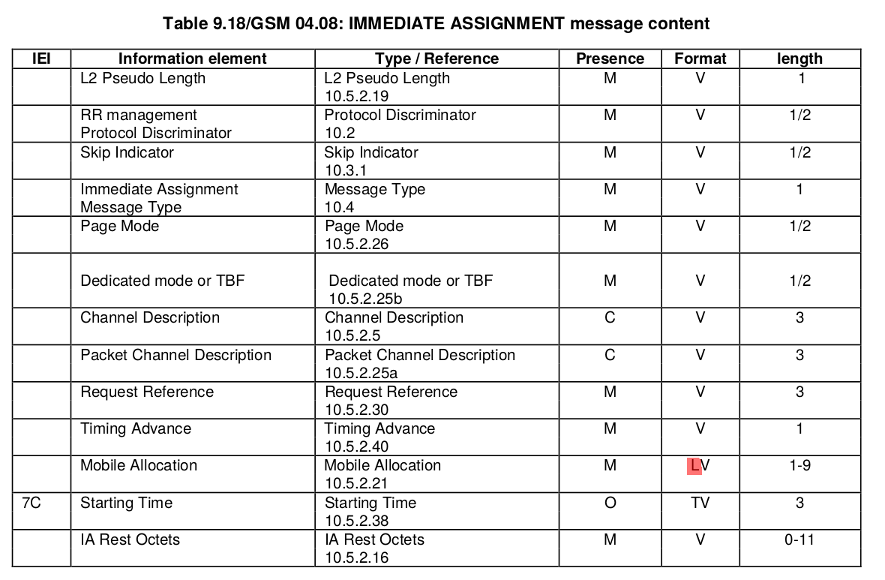
Mobile allocation data is directly copied to a buffer on the stack without checking …
Continue reading